Our Team
We worked together throught summer, meeting multiple times a week, 100% virtually!
Annie Joss
Surp Student
Annie Joss a 3rd year Computer Engineering major from Seattle, Washington. She was excited to work on this project as it intersected her interests in hardware and security with a field she had not studied, power systems. She is an officer for Women Involved in Software and Hardware (WISH) and plays ultimate frisbee on SLO Motion, Cal Poly’s womens club team.

Austin Grassbaugh
Surp Student
Austin Grassbaugh is a 4th year computer engineering major here at Cal Poly. After his undergrad he plans to continue his education here at Cal Poly and apply to the BMED masters program. He hopes to one day be able to work for a biomedical device company outside of the country.

Joseph Callenes
Project Advisor
Joseph Callenes is an assistant professor in the Electrical and Computer Engineering at California Polytechnic State University. He received his PhD and MS in Electrical and Computer Engineering at the University of Illinois in Urbana-Champaign (UIUC). His research interests include computer architecture, fault-tolerant computing, high performance and scientific computing, and low-power design.
Acknowledgements
We want to thank our advisor Professor Callenes-Sloan, for supporting us and pushing our ideas forward throughout the summer. We also want to thank Dr. Poshtan for his advice throughout the summer.
Additionally, we want to thank our project sponsor, Northrup Grumman. Thank you for valuing and empowering undergraduate students by helping make these opportunities possible. And finally, thank you to CENG and the SURP program for making this experience available to us.
A Dynamic Reconfiguration-based Approach to Resilient State Estimation
Abstract
Power Grid Security Problem
- Attack surfaces and complexity increasing with grid modernization
- New advances in AI and ML will lead to increases in attacks and impact
Power systems are critical and disruption of operation could result in significant or fatal consequences
Project Goals
- Identify characteristic of emerging power grids that can be leveraged to improve the resiliency of the system to attacks
- Devise approach to leverage characteristic to improve security of power systems and model results
Emerging Power Grids
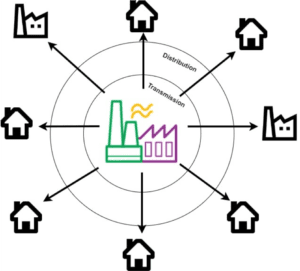
Current Grid
Future Grid
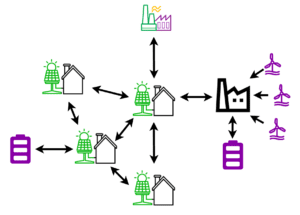
- Shorter transmission distances (at distribution side)
- More complex loads such as renewable energy generation and microgrids
- Reconfigurability of state (generators and storage can charge, be neutral, or discharge)

This project is sponsored by Northrup Grumman
Our Approach: Dynamic Reconfiguration-based State Estimation
The Threat
False Data Injection Attack (FDIA)
- An attacker with access sends false data packets to impact state estimation, which leads to damage across grid
- Research has shown that an attacker can bypass bad data detection and still harm the system if they know the current state of the grid
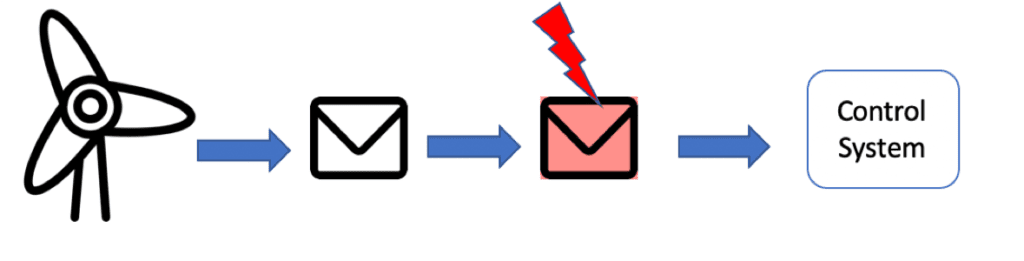
Insight
Reconfiguration
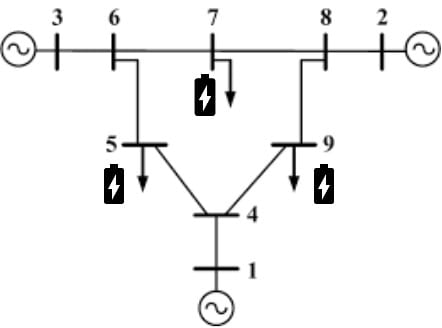
- DERs create a more complex system and makes the grid operate in more than one state
- Leveraging DERs ability to reconfigure the grid into multiple states quickly could improve bad data detection for state estimation against FDIAs.
- An example of DERs is shown below with a modification to the IEEE 9-bus system.
Methodology
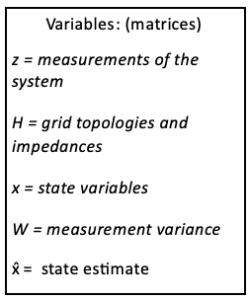
State Estimation
Current measurements:![]()
State Estimate:![]()
Bad Data Detection:
![]()
- Identify K number of stable configurations grid can operate in
- When preforming state estimation, cycle through states for better bad data detection
- If bad data is detected in any of the states, the system has been compromised
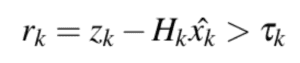
Using multiple states improves amount of false negatives reported by state estimation
Results
One of the major results that we were able to prove is that the different valid configurations do have different rates of bad data detection as shown in the figure below. All of the test systems were modeled with batteries located at loads at 33% of the buses in the system. All the batteries were modeled to have a capacity of 30% of the load they were located at. Due to this result that different configurations have differences in detection rate, if one wants to improve bad data detection they may favor one configuration over others or periodically switch to that configuration to then run bad data detection. This supports our idea that the ability of the system to reconfigure to multiple acceptable states allows bad data detection to be improved
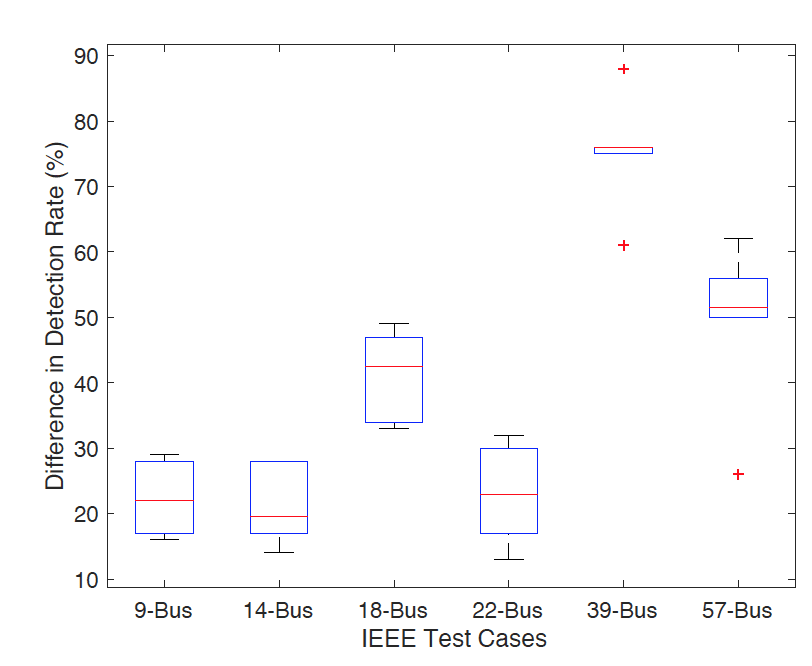
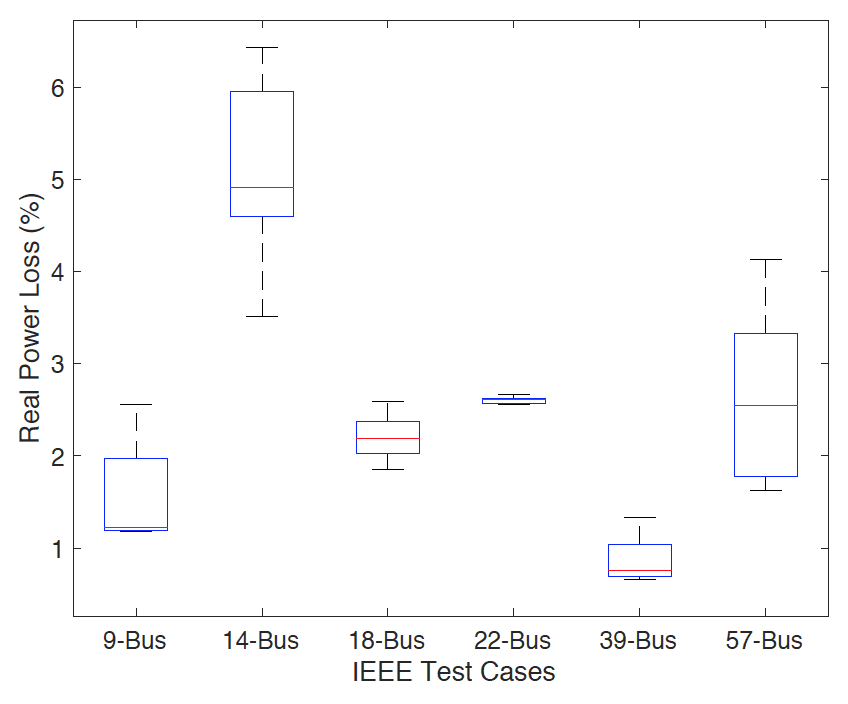
One thing to note when proposing this idea is that these different configurations do incur different costs. On one hand, different states of the battery will require different amounts of generation to account for the changes in the system. However, the total change in generation will be near zero as increased generation when batteries are charging will be accompanied by eventual decrease in generation when batteries are discharging. Another cost we consider is difference in power loss that occurs as shown below. Although this is a cost, the average power loss in all systems is below 5% which isn’t very high especially when considering the benefits of having a more robust bad data detection system.
Conclusions
For this research, a novel method to improve bad data detection in static state estimation was proposed. The approach utilizes the idea of reconfigure-ability to change the topology of the grid, accumulating the state estimation for each topology to improve state estimation. Six different test grids were simulated using Matpower to explore the effectiveness our the strategy.Results found that bad data detection does vary in efficiency at different configurations. Both static and dynamic FDIA detection can be improved under certain configurations, though it should be considered that some test grids had configurations that were as effective as the combined bad data detection.
Sources
[1] R. Deng, P. Zhuang and H. Liang, “False Data Injection Attacks Against State Estimation in Power Distribution Systems,” in IEEE Transactions on Smart Grid, vol. 10, no. 3, pp. 2871-2881, May 2019, doi: 10.1109/TSG.2018.2813280.
[2] M. A. Rahman and H. Mohsenian-Rad, “False data injection attacks with incomplete information against smart power grids,” 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, 2012, pp. 3153-3158, doi: 10.1109/GLOCOM.2012.6503599.